
Cybersecurity requirements for operators and authorities in public transport tenders
Cybersecurity has rapidly become a necessary element for today’s public transport
As our public transport sector becomes better connected, adapting its services to meet the ever evolving expectations of its users, it brings with it the daily risk of cybersecurity attacks.
Cybersecurity attacks have the potential to derail public transport: taking down real-time passenger information systems, hacking of websites and unauthorised access to internal software. While attacks like this do not pose an immediate threat to passengers or employees but they can cause extensive travel delays, network failures and the inevitable loss of passenger trust.
Unfortunately, it is as easy as connecting to a public WiFi network for your personal information to be stolen. So, while providing a free internet connect may be a huge plus for travellers, operators and authorities need to keep their networks safe from hackers. Maintaining the security of data is not only a passenger expectation but a legal obligation of the data controller. Under the European Union’s GDPR regulations, any breach of data confidentiality is an offence punishable by fines of up to 2-4% of sales turnover. Public transport operators and authorities are therefore busy employing a number of measures to prevent such risks from occurring.
Below, are the top cybersecurity threats identified by ENISA, the EU Agency for Cybersecurity, in 2022:
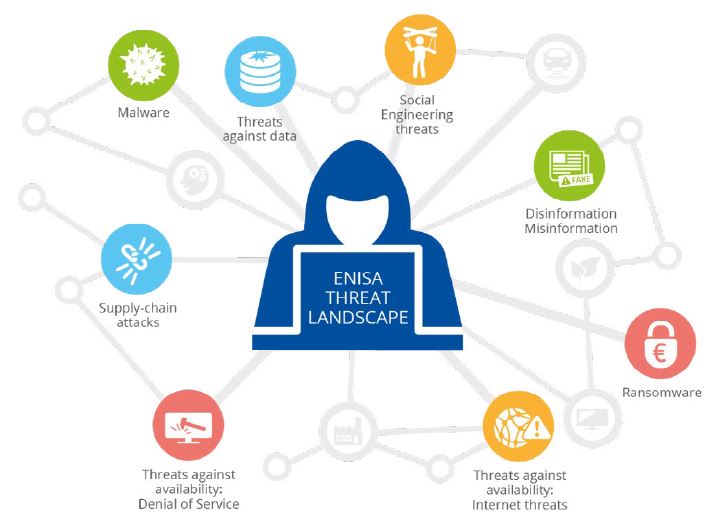
Cyberattacks may affect safety, disrupt entire network operations, ruin the company’s reputation, and generate huge financial losses. That’s why public transport operators must consider coherent cybersecurity protection today in all their processes, especially procurement. The sector cannot afford complacency and must urgently implement the best cybersecurity practices to ensure that it stays that way.
But many operators and authorities fail at the first hurdle
For a safe and a smooth passenger experience, cybersecurity supports the basis of public transport’s digital infrastructure. Yet, when incorporating cybersecurity, many operators and authorities fail at the first hurdle: integrating requirements into their tendering process.
Rather than incorporating the necessary security procedures from the beginning of a metro line expansion or a deployment on new on-demand shared services, operators and authorities often provide requests which are too vague to offer secure solutions to meet their needs. They may then revise their requirements after having experienced certain threats, leading to additional costs and project delays.
From misalignment to meeting cybersecurity objectives
Now, we know that integrating operational cybersecurity requirements is easier said than done, especially as few operators and authorities have the internal specialists who can support the tendering process. In addition to this, the buyers do not provide guidelines to easily assist them in managing the cross-functional process, mostly ending up with a misalignment between operator/authority expectations and the vendor’s services.
Acknowledging the wide discrepancy between what needs to be done during tenders and the resources available for ensuring an appropriate cybersecurity protection, UITP’s Cybersecurity Committee has developed an extensive Report, “Practical guidelines on cybersecurity requirements: Requirements in tendering”.
Key UITP members with the cybersecurity expertise have developed these guidelines for the benefit of operators and authorities, with a comprehensive set of tools and good practices that can be adopted in their procurement process to ensure that cybersecurity objectives are met.
Written by cyber and rail industry experts in close cooperation with public transport Operational Technology Specialists, this Report constitutes the most comprehensive guide for applying best practices in cybersecurity tendering process of the entire transportation market.
The report explores:
- Regulations and legal frameworks
- Procurement process and specification frameworks
- Information security systems specifications
- Cybersecurity technological specifications
Alongside, a reference guide for cybersecurity procurement with references and examples.
Whether applying such a standard to a metro or a bus rapid transit system, these guidelines explain all the necessary steps that must be considered and suggests technologies, their benefits and flaws.

Thank you to the Report sponsors: AXIS Communications, Cylus, INIT and Waterfall Security Solutions!
Join us to discuss cybersecurity & much more in Jacksonville, Florida
We are only a few weeks away from the UITP North America Forum 2023! Co-hosted with Jacksonville Transportation Authority, this is not an event to miss. Cybersecurity is a key topic among others, such as light rail innovations, expanding the functions of stations and the decarbonisation of public transit. Meet and exchange with global transit executives, innovators and seasoned experts. And what’s more, UITP members can attend for free!
opportunities








